Challenges in Mobile Security
In recent years, mobile devices, due to it’s conveniences and ease of use. Mobile phones users have been skyrocketed in all purpose of life from personal to organizational in order to improve quality and productivity. However, the use of mobile devices also open up new areas of vulnerability for potential adversaries to target.
Almost all mobile security threat can be categorized into physical, and network-based, system-based and application-based threats.
Physical Threats
As compared to Desktop and laptop, mobile phone being highly portable and lightweight, which act as double-edged sword. Therefore, loss and theft of mobile devices are one of the most difficult challenge faced in mobile security. Getting physical access to the device would allow attacker to flashing it with malicious system image that will allow to install malicious software or conduct data extraction. therefore, really important to keep device safe along with enforcing certain security measure to restrict un-authorised access to the device.
Network-based Threats
Mobile devices use common wireless network interfaces such as Wi-Fi and Bluetooth for connectivity. Each of these interfaces has its own inherent vulnerabilities and it susceptible to wireless eavesdropping using available tools like Wifite or Aircrack-ng Suite. Thus users only only connect to trusted networks using WPA2 or better network security protocols.
System-based Threats
Most of the manufacturer can sometime introduce vulnerabilities into their devices unintentionally. For instance, the SwiftKey keyboard in Samsung Android was found to be vulnerable to eavesdropping attempts. Security update were subsequently released to fix the issue. I have given one example of it. but even now and then such issues come into picture. Therefore, those incidences need to perform timely updates of mobile device to mitigate system issues.
Application-based Threats
Similarly to system vulnerabilities, third-party applications on mobile devices may also be out-of date. Some application developer do not release software updates in a timely manner or may have dropped support for older OS versions. Even if updates are available user may not update applications on their mobile devices promptly. Using outdated software increases the risk that an attacker may exploits vulnerabilities with these software.
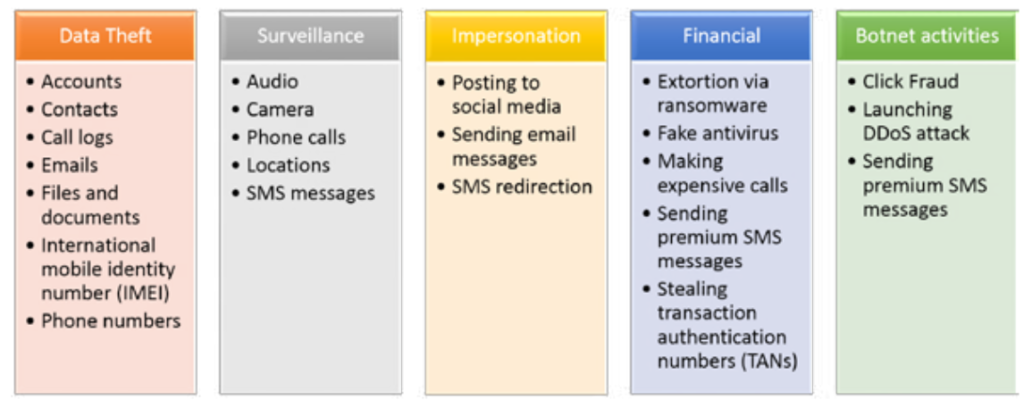
Malicious applications, also known as malware can perform malicious operations when installed on a device such as stealing data, downloading other malwares, sending premium rate messages even remotely controlling a device.

0 Comments