Be a 30 Second E-mail Detective

The universe of email threats is constantly evolving. As email has become central to Government and business communications, attackers have continued to find new ways of using email to breach corporate and government security. From more routine email threats like viruses and spam to advanced targeted attacks like phishing. Attackers use email to send malicious software attacks to an end user. Even when filters are able to find potentially unwanted programs, attackers can still fall back to time-tested social engineering tactics to convince victims to take actions against their own interests.
Some of basic practices that you should follow to avoid those attacks to a certain degree. You have to check out for red flags.
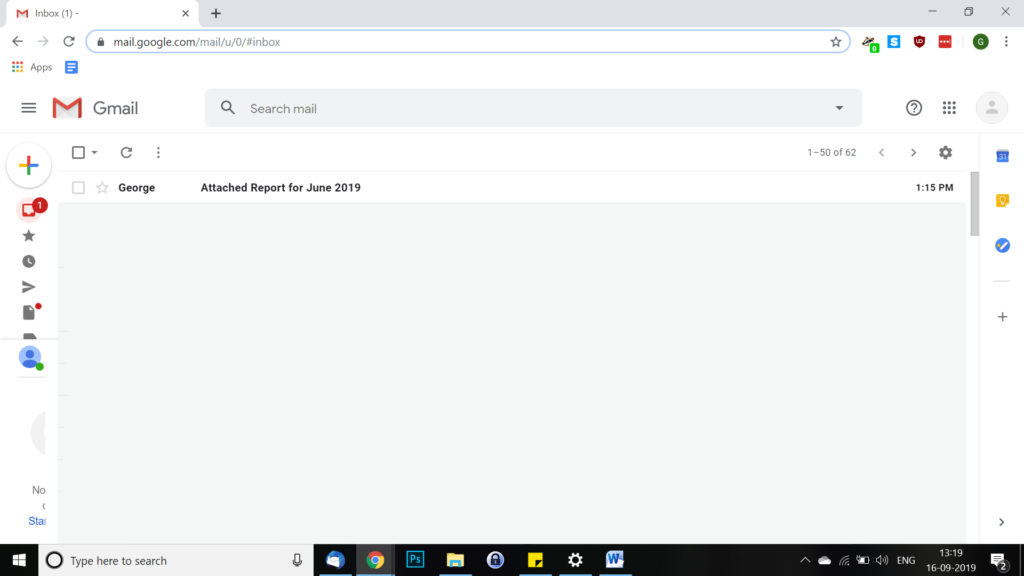
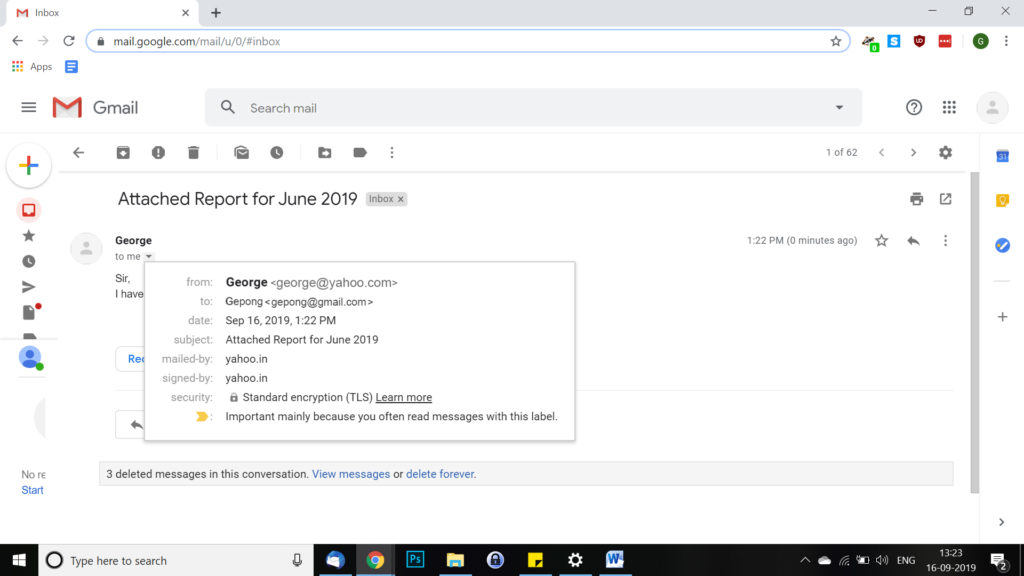
Example, If George usually send you email with gmail but for this email he used yahoo, then its might be red flag.
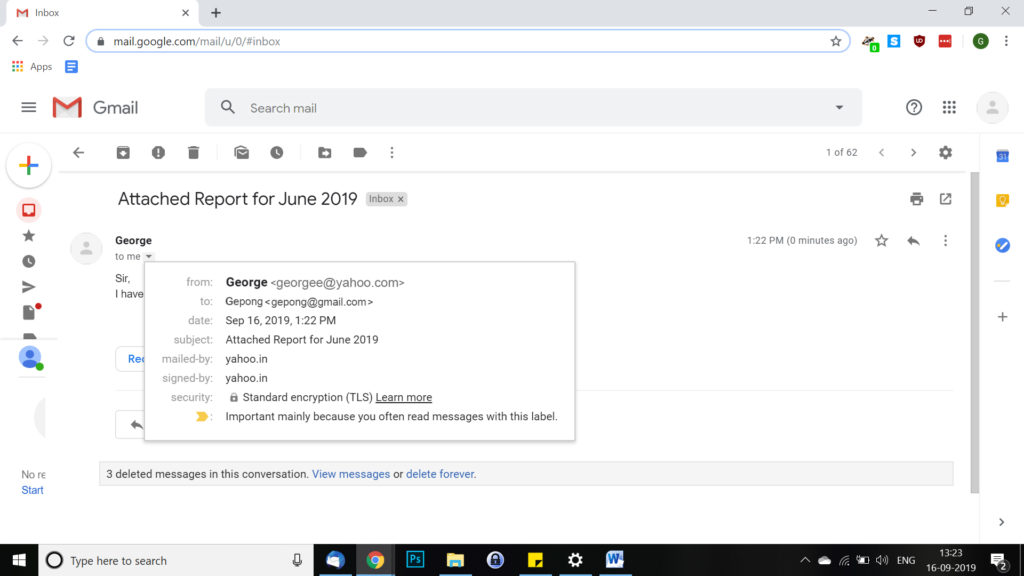
For example, georgee@yahoo.com instead of george@yahoo.com should raise a red flag for you. Even one single (e) makes the E-mail whole different address.


0 Comments