Best Practices for Gmail security.
Email is the most critical aspect of our digital identities, seeing that it can unlock the doors to our other digital accounts and assets. That is why we must secure our email accounts to keep our data from getting into wrong hands. Though Gmail provides powerful security features yet we do not know or use all of them. That is why it is of utmost importance to review and understand the safety features of your inbox — Gmail to secure your account from unauthorized access, hacking attempts, and other malpractices.
1. Create Strong password
The ideal password must include at least – 1) More than 15 characters. 2) Numbers. 3) Uppercase letter. 4) Lowercase letter. 5) Special characters such as ( !@#$%^&*(){}[] ) and 6) Space-bar. in whatever word(s) you choose to use. It should be unique and should not reflect your identity. You can remember it by making meaningless sentence.
Don’t use the same password across different accounts. If a hacker gets the password to one account, they have it for all accounts. And change your password every 6 months to a year because you never know exactly when a password is compromised. You can check the strength of your password on this ( howsecureismypassword.net ).
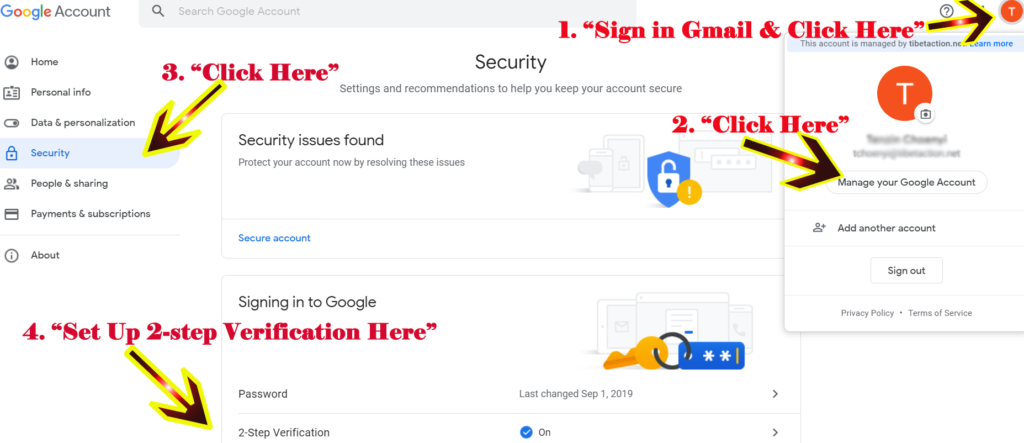
2. Set up 2-step verification
Two-Step Verification is an additional layer of security that you can add onto your Gmail account. When enabled, you will have to enter your password just like usual to log into your Gmail account, and on top of that you need to enter a special code that is sent to your device, or verify the sign in attempt on your phone. This dramatically increases the security of your account and makes sure that hackers can’t get into your account even if the guess or steal your password. Set up at least one backup option so that you can sign in even if your other second steps aren’t available. You can follow the steps shown in the link below on how to set up 2 step verification. (https://learn.tibcert.org/knowledge-base/turn-on-2-step-verification-in-gmail/)
3. Think before click & Detach from attachment
Phishing emails are designed to seem like they are being sent from a real person or company in order to obtain information from you. Bad Attachments and Bad Links can be send through email or social media like chat apps. If it is an attachment :- 1) Preview the attachment first. 2) Right Click on attachment file and copy the link address, then Check it on Virustotal.com 3) Don’t download the attachment, instead add it to your google drive. If it is a link :- 1) Hover over the link and you should see in the left lower corner of the page, the real site that link will take you. 2) Copy the link and check it on virustotal.com. Initiate practice of sending attachment through Google Drive. It is much safer and more efficient.
4. Check crucial account events
An activity log is a helpful security measure to identify and track probable hacking attempts or unauthorized accesses, and Google does maintain an activity log of your account. You must check it regularly and flag any suspicious event, like an unknown account or info update. Let’s see how you can check this log:
- Open “Sign-in & security” in your browser.
- Scroll down and you will see section named “Recent security activity”. Here you will see If there’s security-related activity in your account, like a new sign-in, you’ll be alerted and be able to find details here.
- Below that section, You will see another sections named “Your devices” — check these sections for suspicious events, such as a login from an unknown device or country. Also, you can click “Manage devices” to examine them in detail.
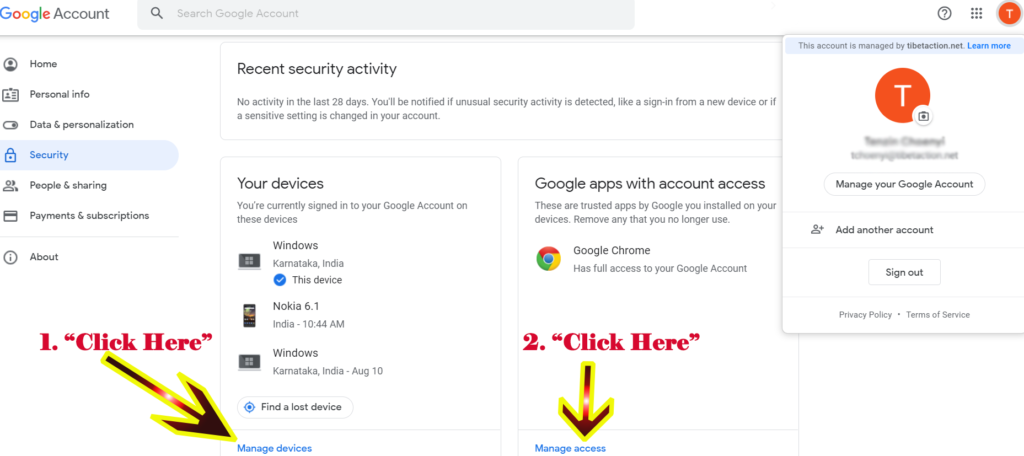
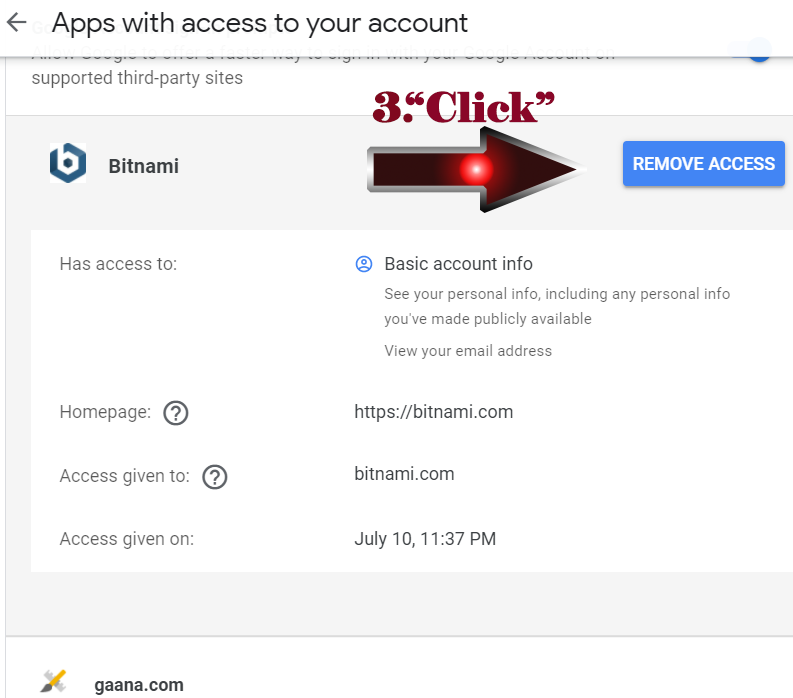
4. On the right side of Section, You will see another sections named “Google apps with account access” — check these sections for apps and remove any that you no longer use. Click “Manage access” and you will see another page with section “Apps with access to your account“. Here you will list of apps that can view your name, email address, and profile picture since you use your Google Account to sign in to those sites and apps previously. So click on any apps and details info will pop up. Here you can click “Removed Access“.
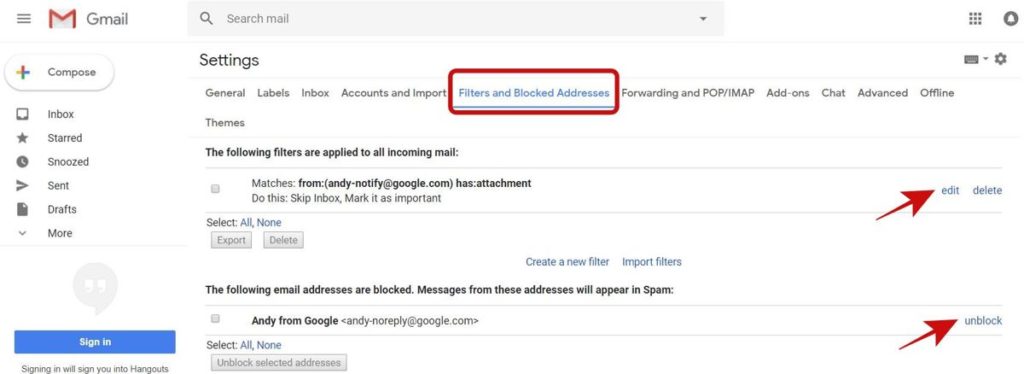
5. Filters and Blocked Addresses tab
Under this tab, you will come across the following:
- Filtered emails: Make sure that you do not have any additional filters. If you do have a suspicious filter, delete it immediately. You can also filter message you do not want to receive here.
- Blocked emails: You can check all the blocked addressed in this section — you will not receive emails from these addresses, so make sure it doesn’t contain any known or essential email address. If it does, unblock it.

0 Comments