Best Practices for mobile security
Almost everyone in 2022 has a smartphone of their own. Be it an iOS or an Android OS phone, their usage is exactly the same. Smartphones have become so advanced over the last decade that the way we use them has changed how we get information, communicate, do business, and live our lives. It holds so much of our personal information that knowing how to secure and protect our data is a luxury in this day and age.
Here are some Best Practices to secure your smartphone.
1. Lock your phone

The lock screen feature on your smartphone allows you to keep stalkers away from your phone and secures your apps and its information. There are many options to choose from on how to lock your device such as PIN, Pattern, Password/Passphrase and Biometrics. For better security we recommend Biometrics such as fingerprint or Face unlock or Password/Passphrase.
2. Check Application Permissions
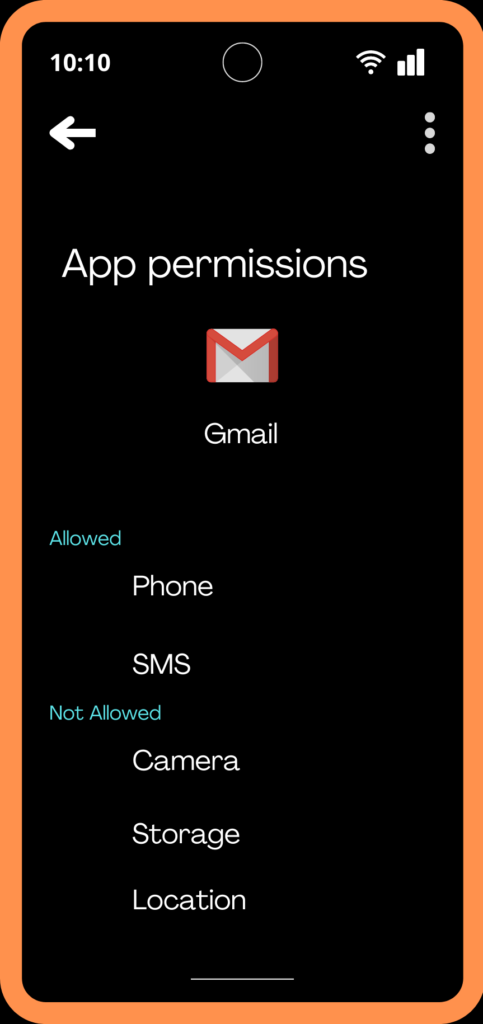
Each app, for its proper functionality, requires a certain number of Permissions to use a device’s basic features and in most cases, we have to grant the permissions for proper functioning of the smartphone. It is through these permissions that the app collects a user’s data and information. But some apps misuses this gateway to harvest a user’s information such as tracking the user’s location, accessing user’s storage files and mobile usage data etc. To put these permissions on check, you can review the permissions given to each app, revoke the ones which are unnecessary and uninstall those which ask for a bunch of unnecessary permissions.
3. Download Application from Official stores

We all need different apps for the various different features each offers but sometimes, to avoid paying for upgrades and to get some app that isn’t available in the region, we opt for third-party alternatives. But these sites being unrecognized cannot be trusted and downloading apps from those platforms can prove harmful to your device.
Therefore, always download apps from Official Stores such as PlayStore or Appstore. As the apps uploaded in these stores go through proper security checks and provide regular updates.
4. Updates your apps regularly
Every now and then developers are working on improving their apps and try to fix issues such as bugs and vulnerabilities that already exist. These fixes and new features are rolled out to users in the form of an update. It might be tedious and annoying to update the apps every other day but you can always check for new contents of an update and decide whether to update or to skip it.
You can also opt for auto-update in the Store settings which automatically updates your app whenever it’s available.
5. Update your OS regularly
Each year Smartphone manufacturers roll out a new version of their OS with new customizable features, UI changes, better security features and fixes and updates on older features.
These device makers also release regular system updates which includes monthly security patches, fixes, device stability and performance updates etc. Therefore, regularly updating your system will keep the device’s security in check and you can enjoy the new features at the earliest.
6. Secure your phone’s email
Every smartphone device requires an Email ID(Gmail, Apple ID etc.) to use the smartphone features. We can also use this Email to create other online accounts, track your device’s location. Therefore protecting and securing your Email is a necessity to keep your device and its data safe. Check out our article on Gmail Security to protect your Gmail account.
Some of Best Practices for Gmail Security are:
- Use Strong Passwords
- Use 2 Step Verification
- Avoid clicking on links and downloading attachments
- Use Google Drive to open attachments
- Conduct 30 seconds detection when opening a new mail
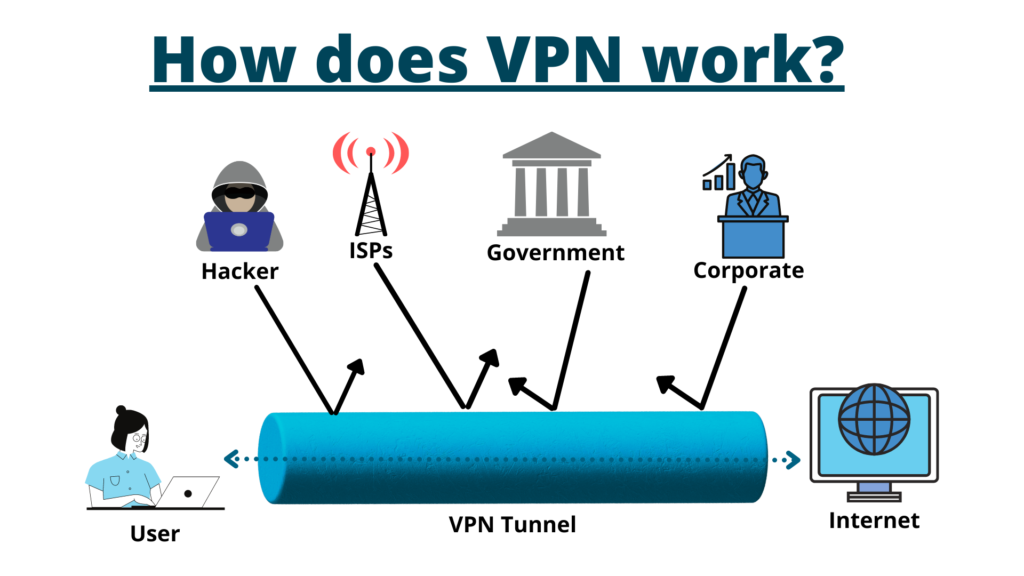
7. Use a VPN
A VPN secures the private network, using encryption and other security mechanisms to ensure that only authorized users can access the network and that the data cannot be intercepted. This type of network is designed to provide a secure, encrypted tunnel through which a remote user can transmit data with the company network.

0 Comments